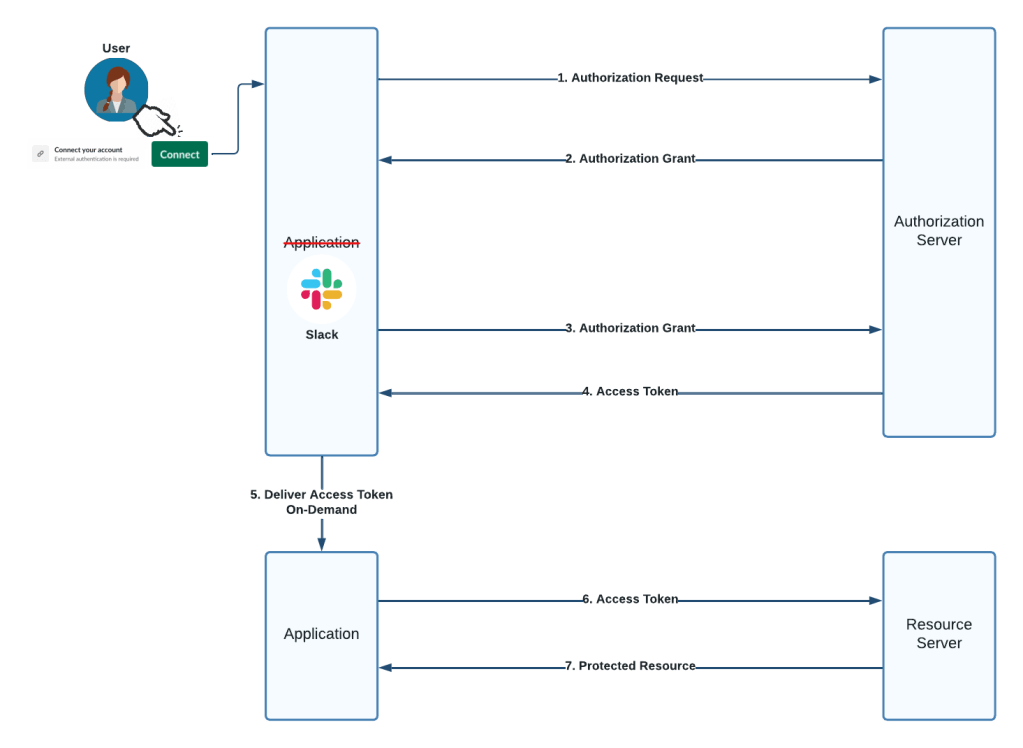
Written by Avinash Reddy Thumma and Scott Nyberg.
In our “Engineering Energizers” Q&A series, we examine the professional journeys that have shaped Salesforce Engineering leaders. In this special edition, we meet Avinash Reddy Thumma, lead threat detection engineer for Salesforce. Based in Hyderabad, India, Avinash’s threat detection team specializes in protecting Salesforce’s network by thwarting malicious threats.
Read on to learn how Avinash and his team have revolutionized threat detection at Salesforce, using an innovative approach that combines advanced correlation and automation platforms to manage tens of millions of threat alerts every day.
What is your background?
My passion is cybersecurity, which I have pursued for more than 11 years. My expertise encompasses cybersecurity incident response, cloud security, threat detection development, digital forensics and threat hunting, and security orchestration and automation.
As the lead threat detection engineer at Salesforce, I oversee the company’s Intrusion Detection System (IDS), a critical line of defense against potential cyberattacks. The IDS monitors and analyzes network traffic to detect any signs of intrusion or suspicious activity.
Before joining Salesforce, I was an incident response and digital forensics engineer, responsible for a global incident response team at another large-scale technology company. That experience gave me an acute understanding for the landscape that Salesforce incident response (IR) analysts face, and I apply that knowledge daily to help our IR team scale with the IDS to counter sophisticated cyberattacks.
What was the greatest challenge your threat detection team faced?
The majority of IDS alerts our IR team received each day turned out to be false positives, where benign network activity was mistakenly identified as malicious. These false alerts resulted from various factors, such as misconfigurations, incomplete threat intelligence, and system glitches. Historically, manual investigation was a time-consuming process and could take 15-45 minutes to evaluate each alert. Analysts found the abundance of false alerts to be counterproductive, eroding their trust in the IDS, reducing efficiency, and causing alert fatigue.
How did advanced correlation and automation help address that challenge?
The threat detection team adopted advanced correlation and automation platforms, which now play a crucial role in managing and analyzing the massive volume of IDS alerts.
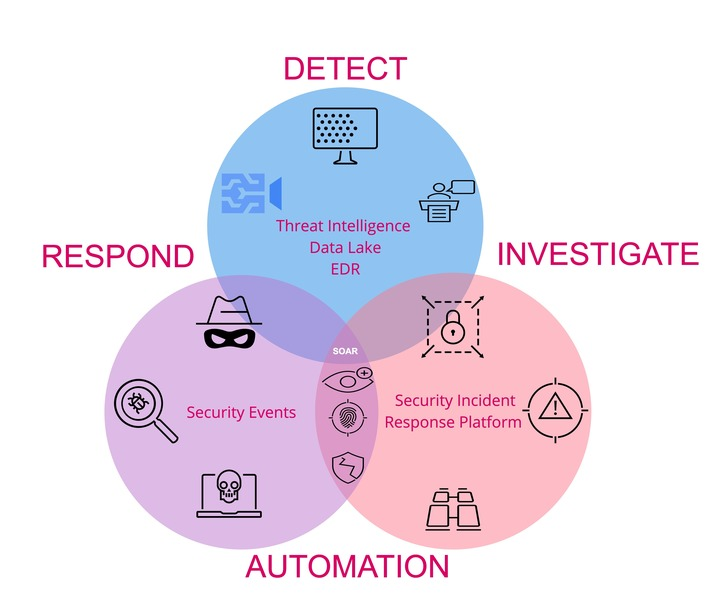
Enhanced correlation and automation effectively detects threats, combatting alert fatigue.
Advanced correlation provides analysts with contextual data necessary for efficient triage of malicious activity. Serving as an enhanced security information and event management solution, the correlation platform aggregates and analyzes logs from the company’s IT data lake environment — including servers, devices, domain controllers, etc. — enabling better interpretation of security events.
Acting as a centralized hub, the automation system seamlessly integrates with sophisticated security tools and automates incident workflows that incorporate customized playbooks, automated triage, alert enrichment, and continuous improvement. As a result, the team reduced the number of false alerts, accelerated threat response times, and significantly minimized manual effort. Analysts now only receive alerts that require their attention, effectively resolving the issue of alert fatigue.
How do your automation and correlation platforms collaborate?
Here is how these systems work in synergy:
- Alerts detected: Network traffic passes through the IDS, which identifies suspicious actors or possible threats, triggering a security event.
- Correlation platform validates events: The correlation platform records the event and cross-references it with a vast amount of log data, creating a highly refined alert for the automation system.
- Automation platform responds to threats: Upon receiving an alert, the automation system executes and automates response actions using enriched data and intelligent playbooks. Codifying response workflows, playbooks drive consistent, efficient, and standardized actions for managing alerts.
- Analyst reviews the threat: The automation system presents the most compelling cases to the analyst for review, automatically closing out less significant cases.
- Continuous updates and scaling: The automation system continuously refines in its detection rules and playbooks by incorporating input from the correlation platform, past incidents, and user feedback. This iterative approach drives ongoing improvements — enhancing the efficiency of the IDS and effectively distinguishing real threats from noise.
What was the time-saving impact of automation on IR analysts?
Analysts reported that automating the closure of a false positive case saved them 15 minutes of work. Extrapolating this across a three-month period, automation saved them a total of 11 days’ worth of effort.
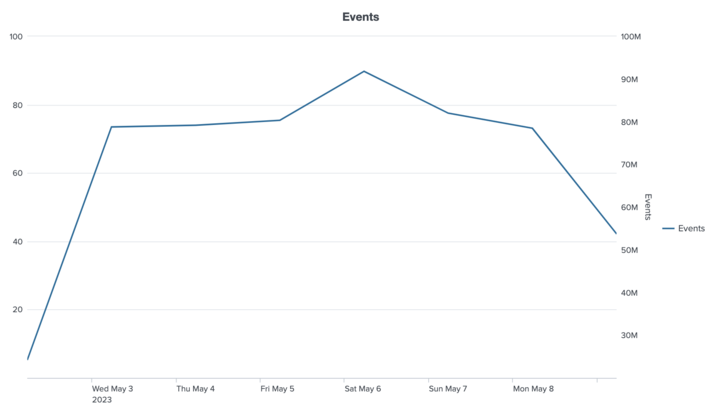
Recently, the IDS tracked as many over 90 million events in a single day, which automation deftly handled, sharing only key events with analysts.
Ultimately, automation provides analysts with instant access to all relevant data when they open a case or review an alert, enabling them to make prompt decisions on whether the incident requires further action.
Learn more
- Interested in more automation stories? Read this blog to learn how India’s Salesforce Engineering team uses automation to reduce customer processing time from hours to seconds.
- Stay connected — join our Talent Community!
- Check out our Technology and Product teams to learn how you can get involved.
- Discover the latest best practices for cybersecurity. Check out the Salesforce Security Blog.