By Krishna Pandey and Scott Nyberg.
In our “Engineering Energizers” Q&A series, we examine the professional journeys that have shaped Salesforce Engineering leaders. Meet Krishna Pandey, Director of Security Engineering at Salesforce. Based in Bangalore, India, his Application Security Technology (AST) team powers Salesforce’s source code security program, charged with using AI to detect and eliminate various types of secrets in code.
Read on to learn how Krishna and his team overcome challenging obstacles to provide application and service owners with comprehensive visibility and timely remediation through context-specific, high-quality, and actionable application security findings.
What are secrets in code and how does AST address them?
Secrets in code are sensitive information that is embedded directly within source code.
AST provides a comprehensive AI-powered Credential Scanning Service (CSS) that integrates seamlessly with development workflows and prioritizes developer experience. This enables AST to detect and prevent secrets from entering into source code, enhance triage processes, and streamline the detection and remediation of secrets in code.
Krishna shares what keeps him at Salesforce.
What are examples of secrets in code and what are potential consequences if secrets are unaddressed?
Some examples of secrets that CSS can detect include AWS secret keys, GitHub tokens, customer API keys, and database passwords. If these secrets are unaddressed, they can lead to severe consequences such as exposing sensitive data, compromising proprietary source code, or allowing unauthorized access to customer information.
For instance, AWS secret keys can provide access to the entire AWS account and its resources, potentially exposing a large amount of data. Stolen GitHub tokens may expose a company’s proprietary source code, which is crucial for maintaining a competitive advantage. Customer API keys, if leaked, could grant hackers access to customer data, while database passwords could expose sensitive information like personally identifiable data or personal health information.
What are the top challenges your team has faced in eliminating secrets in code?
AST encountered two main challenges for eliminating secrets in code:
- Attribution: With ~120,000 repositories that were created over long periods of time, combined with issues of deactivated users and users switching teams or projects, attributing ownership of code repositories was challenging. In response, AST collaborated with other engineering teams to programmatically update ownership information and establish policies for inactive or archived repositories.
- Different SCM types: Onboarding different types of source code management (SCM) systems hosted on different networks with varying levels of trust presented a hurdle. Consequently, AST went through multiple security assessments to expand coverage across different business units, which helped resolve the issue in a secure way.
Krishna describes Salesforce Engineering’s unique culture.
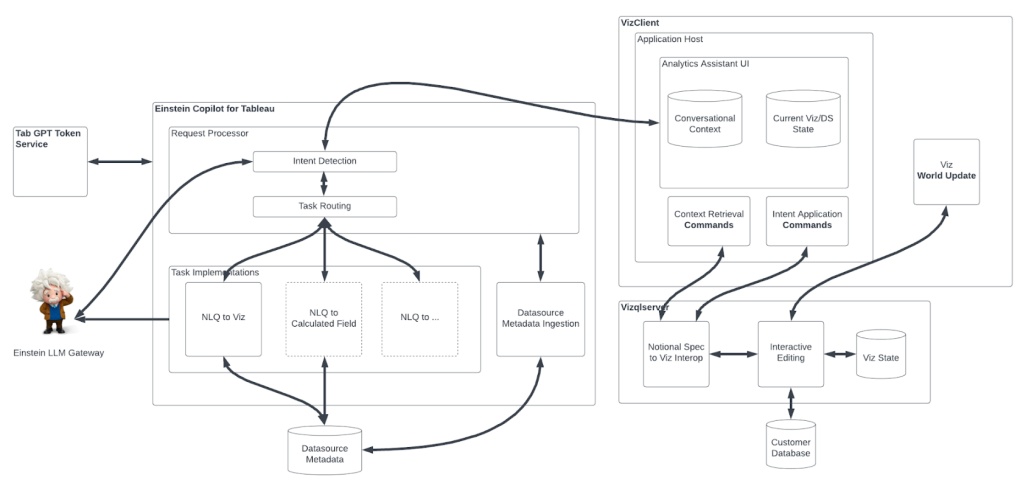
Please walk us through the steps for using AI to detect and remediate secrets in code.
AST provides a seamless and efficient workflow for detecting, triaging, and remediating secrets in code, enhancing the security of its applications and services.
The entire workflow is automated, removing the need for manual intervention, while empowering AST to seamlessly scale its secret detection and remediation efforts.
As a developer attempts to check their source code, AST’s CSS — which is integrated into the development pipeline — automatically scans the code to detect any potential secrets. The service internally uses repositories or org-specific triage information, ensuring that only valid and relevant secrets are flagged for further action.
If secrets are found, CSS creates a security bug ticket, applying a severity-based SLA policy to ensure timely remediation. Remediation includes:
- Triaging the secret. Developers log into a developer portal for triage to see detected findings from various security tools, find the secret’s coordinates, and assess its validity.
- Rotating the secret. Developers rotate the exposed secret, changing the password or key to ensure it cannot be leveraged by malicious actors.
- Storing the secret securely. Developers store the secret within Salesforce’s approved secrets management solution to prevent further exposure.
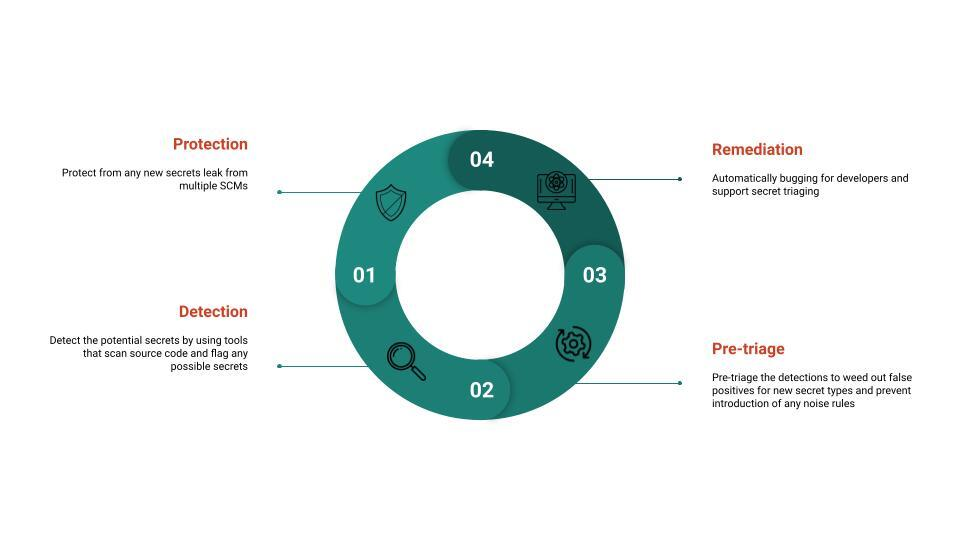
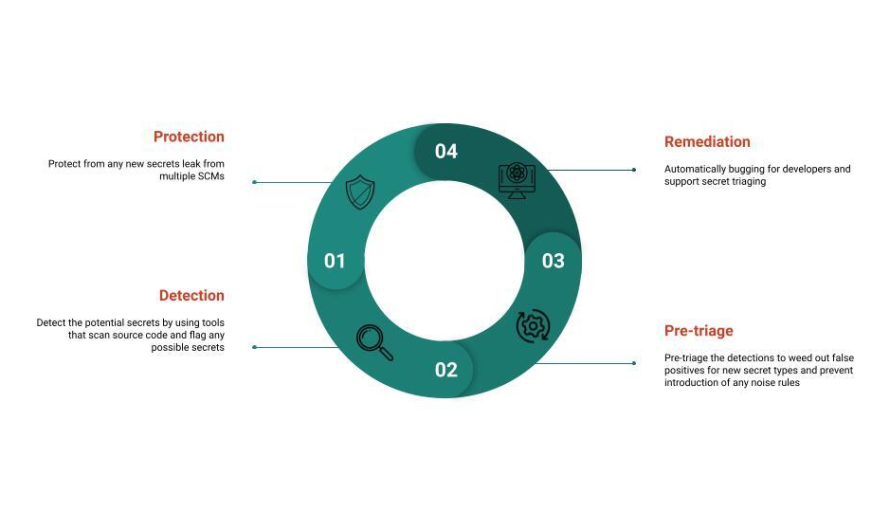
Can you provide insights into AST’s overall progress in eliminating secrets in code?
Our team has made significant progress in eliminating secrets in code through a phased rollout approach.
AST began by introducing blocking and bugging for high-severity secrets in batches for selected organizations and SCMs. This allowed the team to gradually increase coverage while maintaining a controlled signal-to-noise ratio through pre-triage processes. By ignoring test files, documentation, known patterns, and third-party open-source code, the team ensured that only relevant secrets were flagged. This approach enabled them to detect and remediate potential critical risk in the form of credentials across Salesforce by working closely with a fellow internal team to determine the appropriate severity levels for different secret types and implement remediation strategies.
To ensure a consistent developer experience, AST later implemented features such as de-duplication of results produced by multiple tools. Additionally, the team collaborated with the Security UI team to develop a highly scalable platform and APIs, supporting a large number of concurrent developers.
Most recently, AST improved scan time and availability of its secret scanning service, ensuring that integrated and dependent systems can meet their high availability goals.
Learn more
- Read this blog to learn how India’s Global Computer Security Incident Response Team uses cutting-edge automation tools for alert response and malicious threat containment.
- Stay connected — join our Talent Community!
- Check out our Technology and Product teams to learn how you can get involved.
- Discover the latest best practices for cybersecurity. Check out the Salesforce Security Blog.