
Written by Ping Yan, with Anuj Malkapuram and Soundarya Balasubramani
Background on Credential Stuffing
Credential stuffing, in its simplest sense, is a type of cyberattack involving stolen account credentials. It is also known as “password spraying” or “credential spills.” Whenever there’s a data breach — and there are about 30 that happen every week on average — attackers get hold of a large amount of usernames and passwords. They then use them to gain unauthorized access to user accounts through large-scale automated login requests directed against a web application. Imagine having a hundred keys on hand and five locked doors in front of you. You know five of those keys work. All there is left to do is manually insert every key in every lock — except, it’s not manual and you have robots who would do it for you.
According to research conducted by Google, between March, 2016 and March, 2017, 1.9 billion usernames and passwords exposed via data breaches were traded on blackmarket forums. These online breached credentials are exploited by bad actors in various ways toward thousands of online services. Across the internet, Akamai detected approximately 3.2 billion malicious logins per month from January through April 2018, and over 8.3 billion malicious login attempts from bots in May and June 2018.
So let’s understand a little more about this egregious technique used by attackers around the world.
As the attackers find new techniques, so does Salesforce. With an unrivaled customer success platform, protecting our customer’s data and continuing to maintain Trust as our #1 value is paramount. In this blog post, we’ll demonstrate how we combat credential stuffing.
How Salesforce Combats Credential Stuffing
Many credential stuffing detection techniques rely on static rule-based systems and databases of known breached credentials such as HaveIbeenPwned. These methods are static and reactive in nature. It is estimated that an average of 15 months goes by before a breach gets reported, giving attackers plenty of time to play with the data. We need proactive methods that address such attacks with minimal latency.
The detection and defense technology we develop must provide detection for businesses with different traffic volumes and user base sizes located all around the world. Meanwhile, we need to be able to detect as soon as the attack is happening to best protect against account compromises and account take-overs following up a successful credential stuffing attempt. Last but not the least, mitigation is crucial for the accounts that are successfully validated by credential stuffers.
The detection algorithm draws upon rigorous research on the credential stuffing traffic patterns. The detection method is a three-step process comprised of temporal (time-series) anomaly detection techniques, cardinality analysis by endpoint attributes and consolidation of known threat intelligence.
The following diagram depicts the detection components employed by the detection engine.
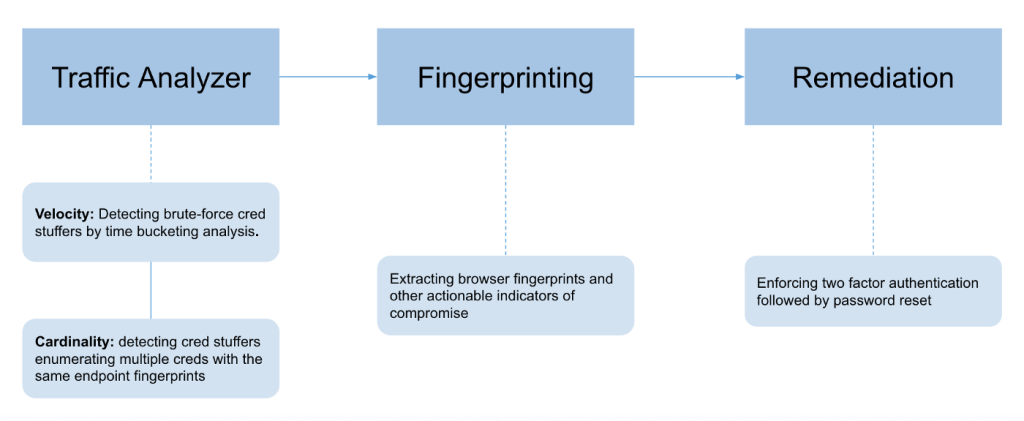
Figure 1: The three-step process followed by the detection and response engine
When accounts are known to be compromised, those account passwords need to be quickly reset to revoke the attackers’ access. Salesforce app initiates an in-app notification requesting Identity Challenge Verification. If the user successfully completes that challenge, they will have to reset their password before accessing Salesforce again.

Figure 2: The remediation mechanism
At Salesforce, we continue to use the most innovative detection mechanisms to safeguard our customers’ data. We continue to improve the visibility for customers and provide them a holistic view through the Salesforce Shield products, specifically Event Monitoring. To learn more about the Event Monitoring service, please visit this page.
What Can You Do To Protect Yourself
Of course, maintaining good hygiene and setting up two-factor (or multi) authentication based on your companies threat model remain recommended security best practices. Here are some additional steps you can take to mitigate your risk against credential stuffing:
- Use two-factor authentication wherever you can, especially on Admin/Privileged accounts.
- Enforce users to use strong and unique passwords (or a password manager). To ensure users are not re-using their old passwords, enforce a password history table.
- Setup rate-limiting and captcha capabilities to your authentication pages.
Salesforce provides its customers a suite of secure authentication and account verification techniques to adapt and apply on their domains, and we recommend you take advantage of those. In the meantime, we will continue to build state-of-the-art detection and response techniques to protect our customers from Credential Stuffing attacks, among other threats.
References
[1] https://static.googleusercontent.com/media/research.google.com/en//pubs/archive/46437.pdf
[2] https://www.prnewswire.com/news-releases/akamai-credential-stuffing-report-shows-financial-services-industry-under-constant-attack-from-automated-account-takeover-tools-300714800.html
[3] https://blog.shapesecurity.com/2018/07/30/the-2018-credential-spill-report/
[4] https://securityboulevard.com/2018/05/59-of-people-use-the-same-password-everywhere-poll-finds/
[5] https://www.cbronline.com/news/global-data-breaches-2018
[6] https://www.salesinsideinc.com/services-details/salesforce-customers-list
[7] https://haveibeenpwned.com/
[8] https://www.wired.com/story/what-is-credential-stuffing/
[9] https://howsecureismypassword.net/
[10] https://developer.salesforce.com/docs/atlas.en-us.securityImplGuide.meta/securityImplGuide/security_auth_configure.htm
[11] https://www.lastpass.com/solutions/business-password-manager
[12] https://trailhead.salesforce.com/en/content/learn/modules/event_monitoring/event_monitoring_intro
[13] 2018 Credential Spill Report, Shape Security






