
Trust is the #1 value of Salesforce, and trust of our customers is of paramount importance. In the 21st century, where all businesses are embracing the Internet, they have to face the reality of the growing number of security threats where the end-goal is often data-exfiltration. We work with hundreds of thousands of companies worldwide and millions of users via an unrivaled customer success platform. Hence, it is of utmost importance for us to protect our customers’ data.
Background on Data Exfiltration
Since the advent of the Web, enterprises have sought to digitize their information and knowledge assets, from financial data, to health records, to sales leads. This digitization exercise has led to a vast number of services being built on the data, unlocking potential — business or otherwise — and advancing enterprises. It is clear now more than ever before that data holds the key to the digital transformation of every industry worldwide.
They say with power comes responsibility. Similarly, with more data comes a bigger attack surface for attackers looking to steal this data and hence a bigger responsibility for the companies collecting it. While the act of data exfiltration itself is self-explanatory, there are different ways through which attackers get access to the data they want to exfiltrate. The attacker could be using malware over a network to gain access to an employee’s computer. Another common way is to deploy a brute force attack technique called credential stuffing, after obtaining credentials from a data breach. Or it could even be a disgruntled employee at the company who leverages the privilege of his or her role to exfiltrate data out. In fact, insider threat is one of the top causes and has been on a steady rise.
With the advent of stricter policies around customer data — GDPR, CCPA, PCI, and more — businesses need to put better protections in place now more than ever. In 2018, the GDPR legislation raised the maximum penalty for contraventions to up to £17.5m ($22.2m) or four percent of global turnover — whichever is greater. Within a year, they found their first offender: British Airways, who were fined up to £183m for a breach of customer data. The very next day, a second culprit was exposed. The ICO announced that it intends to impose a £99 million fine on hotel chain Marriott for failing to protect personal data contained in approximately 339 million guest records. To help protect our customers from such contraventions, our Security Einstein team has developed a machine learning (ML) based solution that can detect anomalous and malicious data exfiltration attempts from Salesforce instances.
How Salesforce Detects Anomalous Data Exfiltration
To start with, it is important to define exactly what ‘anomalous’ means. By definition, an anomaly is something that deviates from the normal. In the specific context of data exfiltration, an ‘anomalous’ attempt can be an attempt of exfiltrating extremely large volumes of data, exfiltrating data from an unfamiliar geographical location (e.g. Antarctica), or exfiltrating at odd hours (e.g. at 3 A.M. on Sunday or during Christmas Eve). Or it can even be an attempt that combines different such oddities. So how do we detect such anomalous events? Enter machine learning.
We glean an understanding of what normal behavior looks like in your specific org by using historical data, say, over the past three months. This data encompasses data about report generation and export, host and network characteristics (browser, operating system etc), login behavior as well as spatio-temporal behavior (geographical location and time of these accesses). Once we build a profile of what constitutes normal behavior, we compare new data export events against this profile and calculate a ‘distance.’ The greater this distance, the more anomalous the data export event. We flag the most anomalous events and bring them to the attention of admins.
Let us consider a few examples. If, for instance a data/report export event consisting of a few million rows is triggered, and if the normal behavior for the org and the user has been to generate and export reports consisting of hundreds of rows, then this is clearly anomalous and we would flag it. Likewise, if the normal behavior of a user in an org is to use Salesforce from where they are based or where they generally travel, we would learn this behavior. So, if a request for data were to come in from a place not seen previously, this would be highly suspicious and we would again flag this data request event as anomalous. Similarly, if a new report was generated at 3 A.M. on a Sunday, but we profiled them as working on Salesforce during regular business hours (Mon-Fri between 8 A.M.-6 P.M.), then this event would be anomalous and flagged.
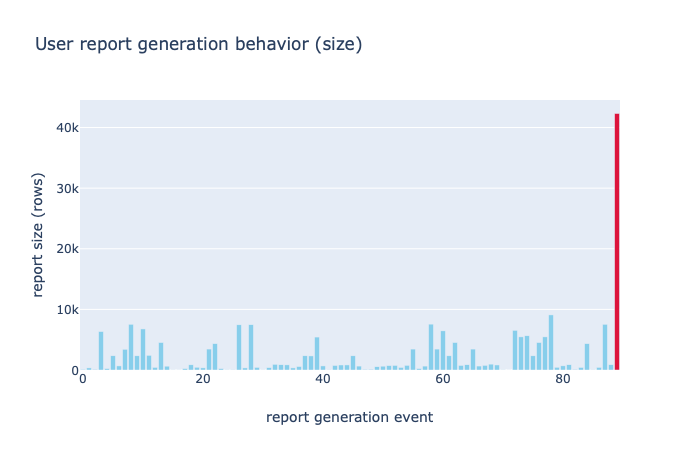
Figure 1: In the example, we look into the report sizes of the reports generated by a typical Salesforce user. We see that all report sizes are generally lower than 10k rows, which can be construed as ‘normal’ behavior, but there is a report request of more than 40k rows, that is clearly anomalous.
A sophisticated adversary however, may adopt strategies to make their behavior seem normal. For instance, the adversary can attempt to extract reports of modest size (hundreds of rows) spread over multiple requests, instead of millions of rows in one request, that will immediately stand out. These are often referred to as low-and-slow attacks. Fortunately, our detection mechanism is sophisticated enough to pick out these events as anomalous as well, as we consider multiple signals to build the profile of normal behavior.
Once we detect such anomalous events, we immediately send an alert to the customer via email with the top contributing factors for the alerts.
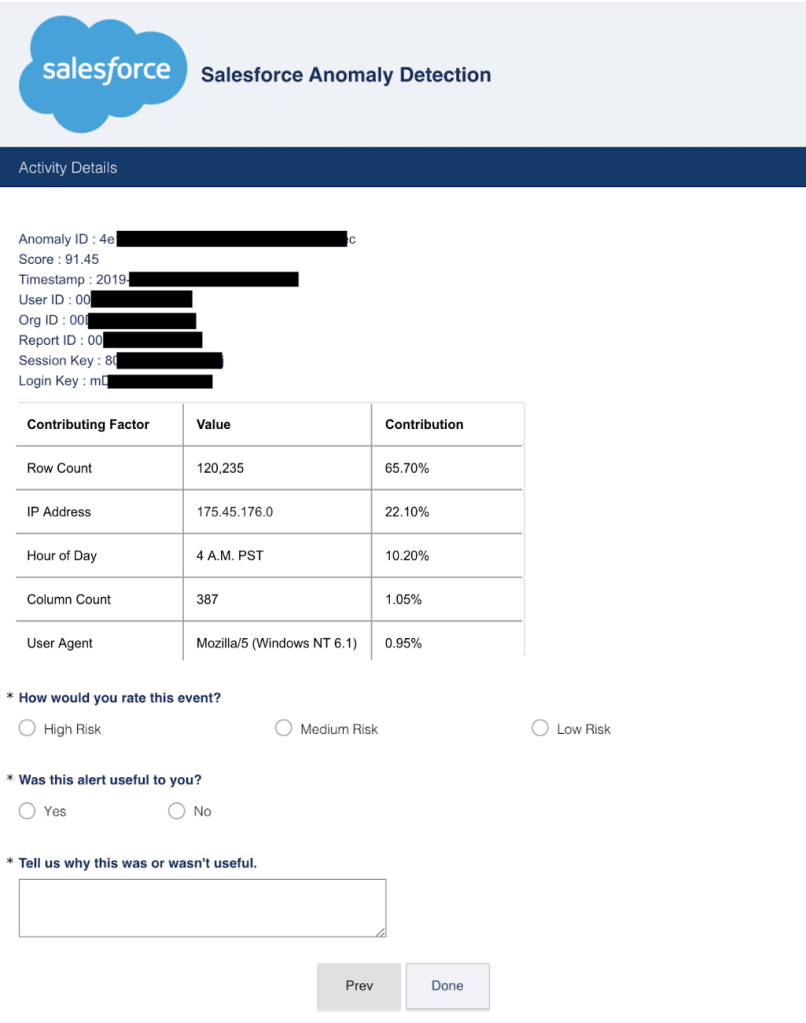
Figure 2: An example event sent to one of our pilot customers
The response pipeline is currently in a pilot stage with a few Event Monitoring customers. If you’re at Dreamforce, learn more directly from the Shield team at their talk, Beat the Hack: Defend from Current and Emerging Threats with Salesforce Shield.
What Can You Do To Protect Yourself
In general, it is always good to ensure high security hygiene in your organization. Some of the practices include: enabling multi-factor authentication (MFA), changing passwords frequently, ensuring your security configurations are up-to-date, enforcing patching, and being educated on phishing attacks, as well as monitoring all activity diligently. However, sometimes all of these measures may not be sufficient. Consider the case of the malicious insider who may have all necessary permissions and settings to access sensitive data. In such a case, the pilot program that carries our solution may help save the day. If you’re a current Event Monitoring customer, find more information here on how you can sign up.
References:
[1] https://www.imperva.com/learn/application-security/owasp-top-10/
[2] https://www.salesinsideinc.com/services-details/salesforce-customers-list
[3] https://www.forbes.com/sites/bernardmarr/2018/05/21/how-much-data-do-we-create-every-day-the-mind-blowing-stats-everyone-should-read/#45feedb360ba
[4] https://www.observeit.com/blog/what-is-data-exfiltration/#targetText=Definition%20of%20Data%20Exfiltration&targetText=Insider%20threat%20incidents%20are%20one,(or%20someone%20else’s)%20gain.
[5] https://www.observeit.com/blog/2019-verizon-data-breach-investigations-report-shows-spike-in-insider-threats-our-top-3-takeaways/
[6] https://www.computerworld.com/article/3412284/the-biggest-ico-fines-for-data-protection-breaches-and-gdpr-contraventions.html
[7] https://www.theguardian.com/business/2019/jul/08/ba-fine-customer-data-breach-british-airways
[8] https://www.businessinsider.com/marriott-hotels-fined-over-2018-data-breach-uk-ico-gdpr-2019-7





