By Amit Chakrabarty, Prabhat Singh, and Sanjeev Chhabria.
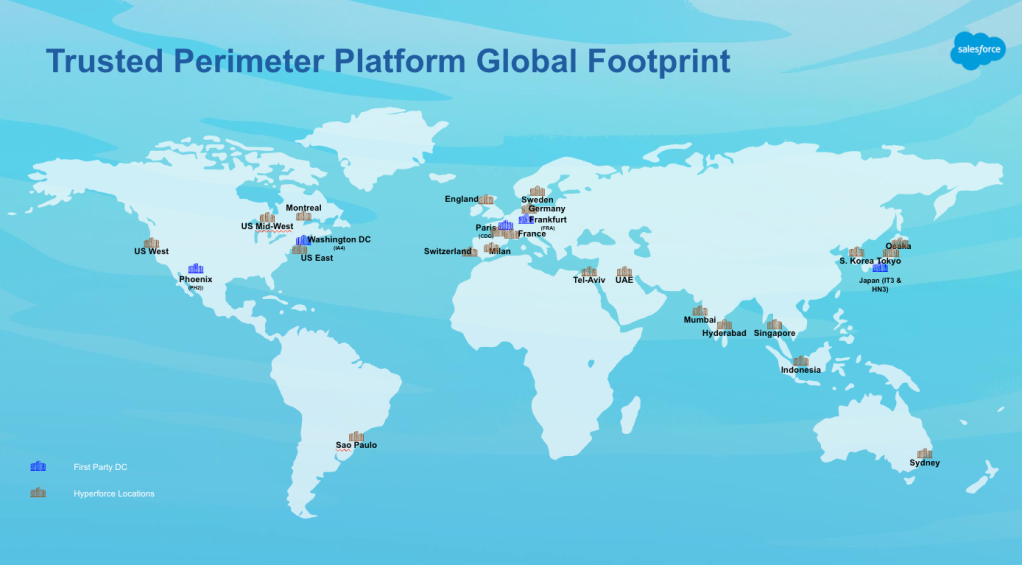
In our “Engineering Energizers” Q&A series, we highlight the engineering minds driving innovation across Salesforce. Today, we feature Amit Chakrabarty, Senior Director of Product Management. Amit collaborated with Salesforce’s Hyperforce Secure Networking engineering team on the development of the Trusted Perimeter, a secure edge platform that acts as the first line of defense for more than 4.5+ million domains across multiple global locations.
Explore how the team built the Trusted Perimeter to fend off DDoS attacks of up to 1.6 terabytes per second from 2 million unique IP addresses in 130 countries, engineered a 10-minute global rollback capability across multiple components, and integrated AI-powered threat detection systems to identify and mitigate sophisticated attacks in real-time.
What is your team’s mission as it relates to the Trusted Perimeter?
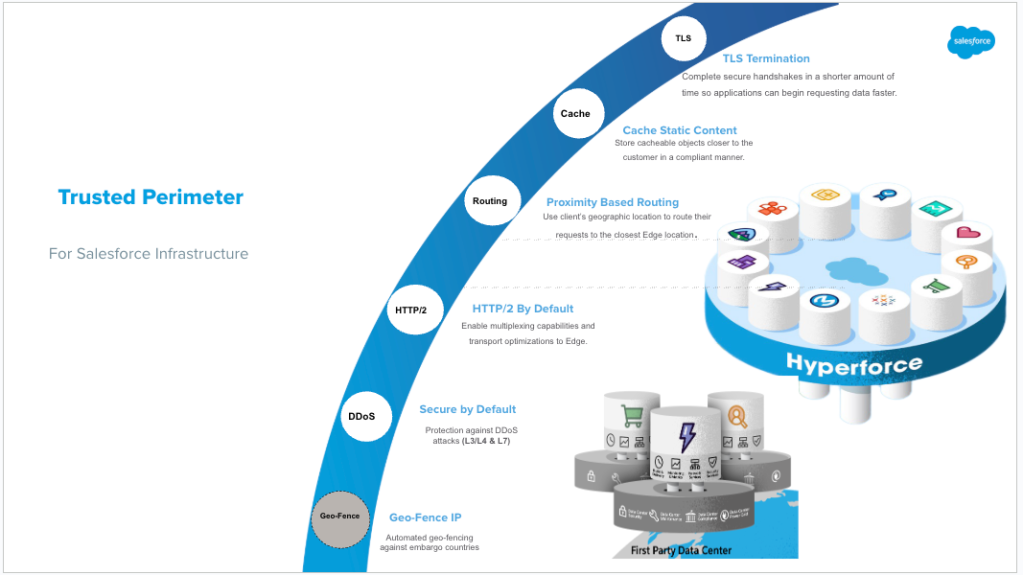
The team is dedicated to building and operating the Trusted Perimeter, our unified edge infrastructure. This digital drawbridge serves as the single entry point for all customer interactions with Salesforce properties, ensuring seamless security and performance no matter where in the world the user is located.
The Trusted Perimeter platform is designed to handle a wide array of critical functions, including TLS termination, enterprise-grade CDN caching, Layer 3/4 and Layer 7 DDoS protection, and support for the latest HTTP/2 and HTTP/3 protocols. It also features geofencing capabilities, which block access from embargoed countries. Whether enterprise customers are booking flights or guests are making reservations through Salesforce-powered applications, the Trusted Perimeter guarantees a consistent and secure experience from any part of the globe.
Each month, the team processes nearly 1.5 trillion transactions for over 3 million customer organizations, with projections indicating an annual volume of 20 trillion transactions. The team faces several attacks daily, and multiple complex DDoS attacks occur weekly, each with the potential to cause significant service disruptions. However, the Trusted Perimeter is designed to handle these challenges transparently, without burdening customers with the complexities of certificate management, protocol optimization, or security concerns. This ensures that our customers can focus on their core business operations while we manage the security and performance at an unprecedented scale.
What global scalability challenges did your team face — and how did you achieve 10-minute rollbacks?
Building the Trusted Perimeter Platform presented the team with two significant challenges: maintaining 99.99% availability, which translates to just 52 minutes of acceptable downtime annually, and operating the platform across a globally distributed architecture that processes trillions of transactions. Traditional deployment methods were insufficient for managing software updates, infrastructure maintenance, and incident response in such a vast and complex environment.
The solution came through the development of a Blue-Green deployment architecture tailored specifically for the Trusted Perimeter, equipped with advanced traffic management capabilities. This approach involves comprehensive configuration management systems and optimized data structures, enabling the platform to handle millions of domain configurations simultaneously. By using a warm standby methodology, all Trusted Perimeter provisioning and configuration remain ready, making deployment as simple as traffic redirection rather than system provisioning.
Most critically, the team achieved a 10-minute global rollback capability across the Trusted Perimeter’s services across all locations. When issues arise, they can swiftly revert the entire infrastructure to its previous stable state through automated rollback mechanisms.
The technical implementation required fundamental innovations, including custom traffic routing algorithms. These algorithms allow the Trusted Perimeter to process complex routing decisions across multiple data centers while maintaining consistent performance, a feat that traditional methods could not achieve at Salesforce’s transaction volumes.
What nation-state attacks were overwhelming your defenses — and how did AI detection stop them?
The Trusted Perimeter is constantly evolving to stay ahead of a threat landscape where attackers are becoming increasingly sophisticated. These threats range from nation-state actors to well-funded cybercriminal organizations, which can launch attacks of up to multipleterabytes per second from millions of unique IP addresses spread across 130+ countries. Such massive, coordinated attacks pushed the team to innovate beyond traditional rate-limiting and signature-based detection methods.
For example, zero-day vulnerabilities like the HTTP/2 rapid reset attack have impacted the entire internet industry, requiring the team to develop immediate protocol-level defenses within the Trusted Perimeter. Similarly, Log4J-style attacks exploit application vulnerabilities using malformed payloads designed to bypass standard security measures. Nation-state campaigns often involve advanced planning and significant resources, often aligning with geopolitical events.
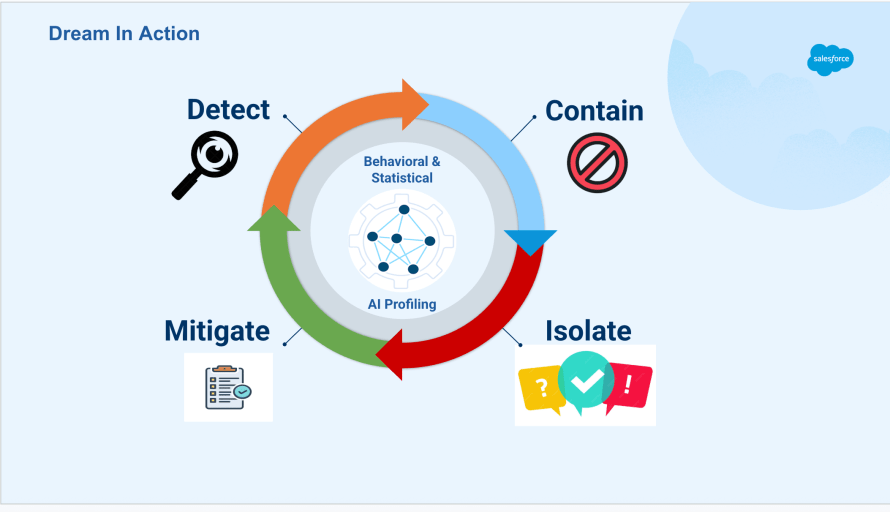
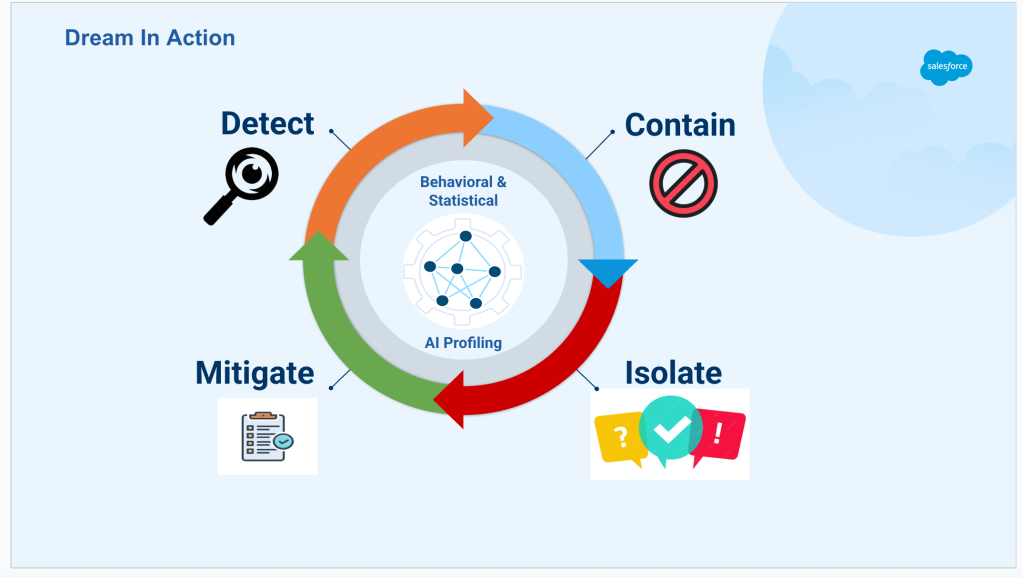
To tackle these challenges, the team developed and integrated AI-driven defense systems into the Trusted Perimeter. These systems use behavioral analysis to establish normal traffic patterns and statistical anomaly detection to spot unusual coordination across vast request volumes. This multi-layered approach allows the Trusted Perimeter to handle attack scales that would be impossible for human analysts to manage, identifying malicious activity within seconds of an attack starting.
The team also developed proprietary algorithms that create precise mitigation plans to block attack traffic while ensuring legitimate users can still access the platform. These algorithms analyze attack characteristics in real-time and implement specific filtering rules within seconds, minimizing customer disruption and maintaining service availability across the global network.
How do you respond to rapidly and constantly changing cyber threat landscape while maintaining high service availability and reliability?
Operating the Trusted Perimeter involves unique challenges where external adversaries impose unpredictable timeline pressures. Unlike traditional software development with set release schedules, security threats can emerge at any time, requiring platform updates within hours or even minutes. This high-stakes environment demands immediate modifications for nation-state attacks and zero-day exploits and attacks, with virtually no tolerance for errors.
To meet these challenges, the team has implemented zero touch automation and AI-enhanced quality processes. They developed automated testing frameworks that validate all Trusted Perimeter changes through multiple scenarios before deployment, ensuring code quality even under urgent timelines.
AI integration further boosts quality and speed through automated code reviews, quality analysis, and proactive issue identification. These systems analyze changes across hundreds of components simultaneously, catching potential conflicts or performance issues that human reviewers might miss under time pressure.
The team also adopted a blue-green architecture for safe and rapid releases. Changes are first deployed to a standby environment for thorough validation. Once confirmed as stable and secure, traffic is switched to the new environment. If issues arise, traffic can be quickly redirected back to the previous stable environment within minutes, avoiding lengthy rollback procedures.
This combination of automation and AI-assisted development enables the team to respond rapidly to threats while maintaining the Trusted Perimeter’s high reliability standards.
What type of DDoS attacks put customers at risk — and how did AI play a role in solving this?
Layer 7 volumetric DDoS attacks on the Trusted Perimeter can reach hundreds of millions of requests per minute, globally distributed with sophisticated coordination. These attacks are crafted to appear authentic initially, making traditional signature-based detection ineffective. The shared infrastructure challenge adds complexity, as the team must ensure other customers are unaffected when one is under attack.
To combat this, the team developed AI-powered detection systems integrated into the platform. These systems establish baseline traffic patterns for each customer and region, enabling rapid detection of deviations within seconds. They also use statistical anomaly detection to identify subtle coordination patterns indicative of distributed attacks.
Real-time mitigation is essential.. The team created intelligent systems that generate precise mitigation plans by analyzing attack characteristics and implementing filtering rules within seconds. The team operates 24×7 intelligent incident response using AI agents, ensuring continuous operations and full recovery within seconds of mitigating an attack.
Learn more
- Stay connected — join our Talent Community!
- Check out our Technology and Product teams to learn how you can get involved.






